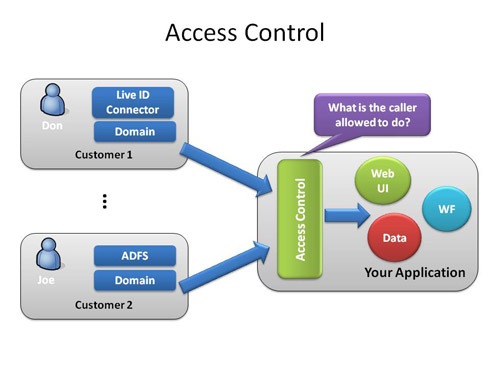
Cloud Security Considerations: Authentication / Access Control and Account Privileges - Accudata Systems
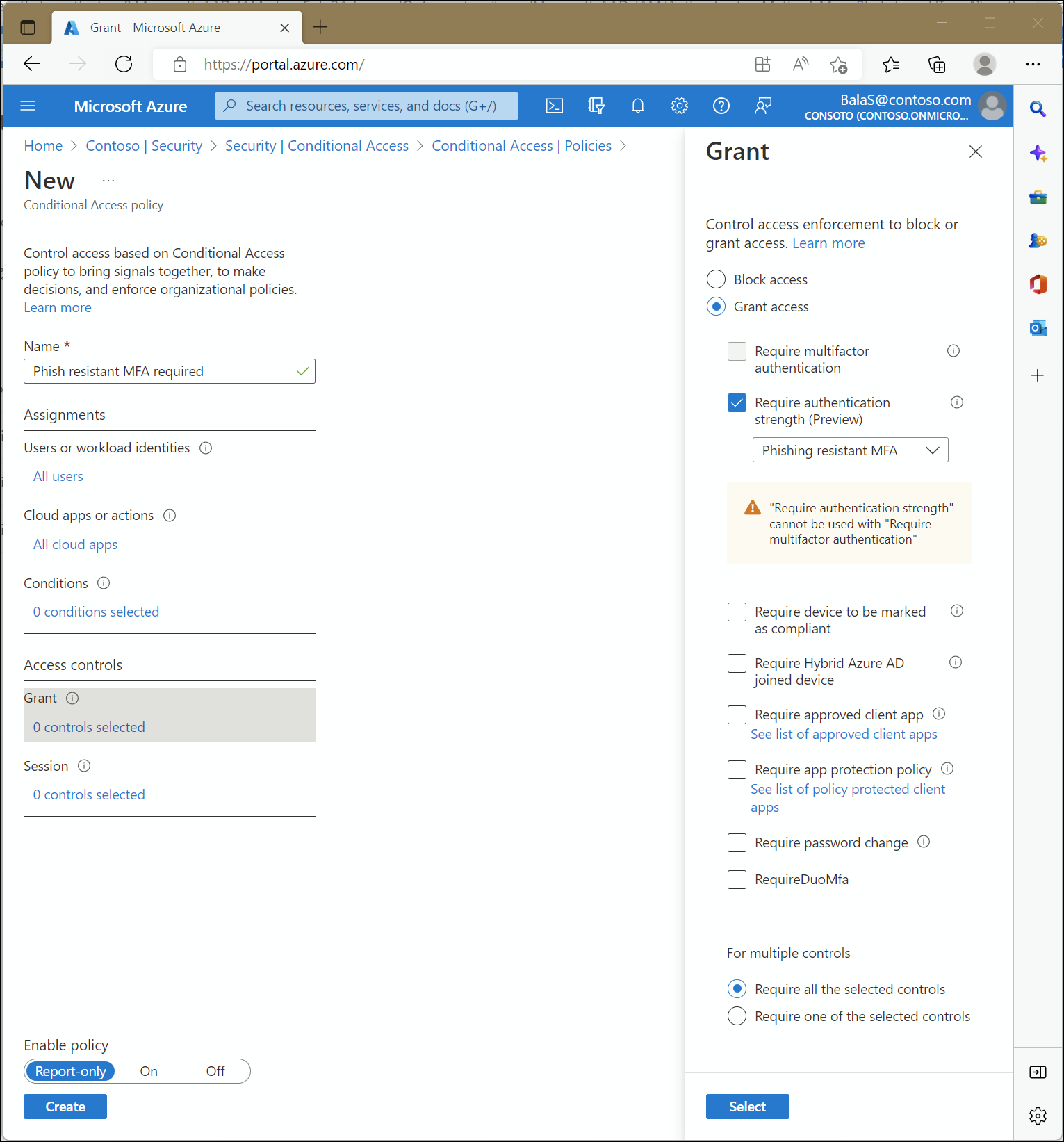
Overview of Azure Active Directory authentication strength (preview) - Microsoft Entra | Microsoft Learn

Vulnerabilities in Single Sign-On services could be abused to bypass authentication controls | The Daily Swig
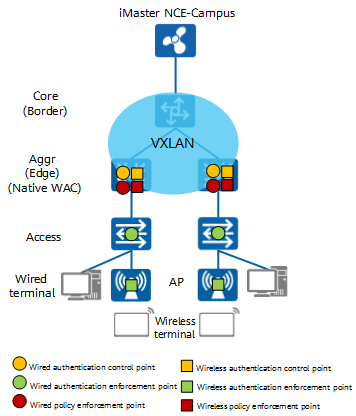
Authentication and Access Control Use Case Diagram for Cloud-based C4I... | Download Scientific Diagram

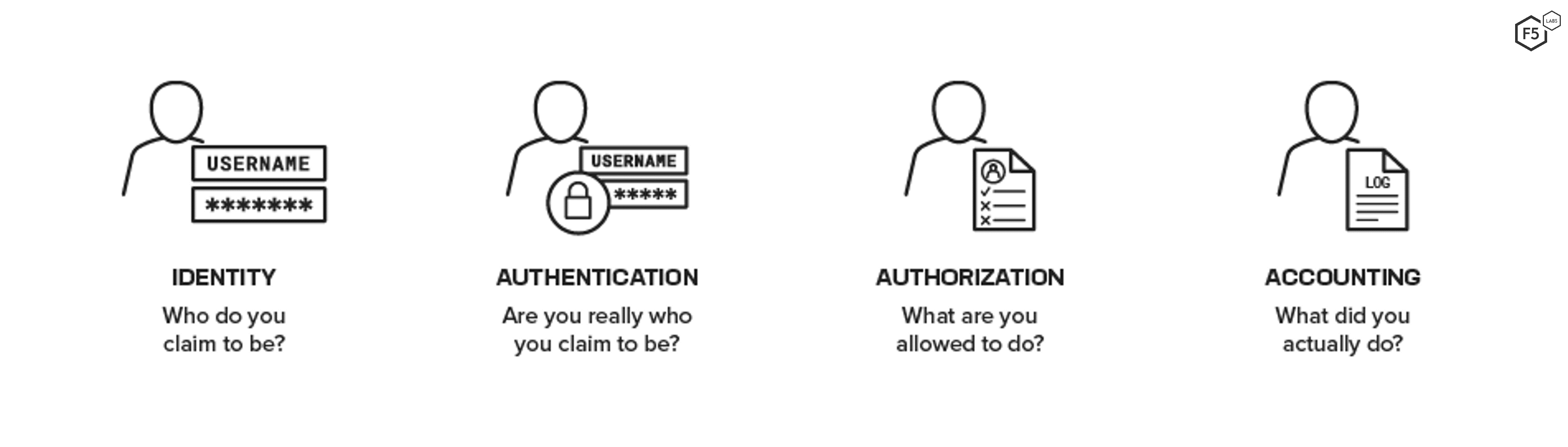
![Access Control Process - Access Control and Identity Management, 3rd Edition [Book] Access Control Process - Access Control and Identity Management, 3rd Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781284198362/files/images/9781284198355_CH01_FIGF01.png)