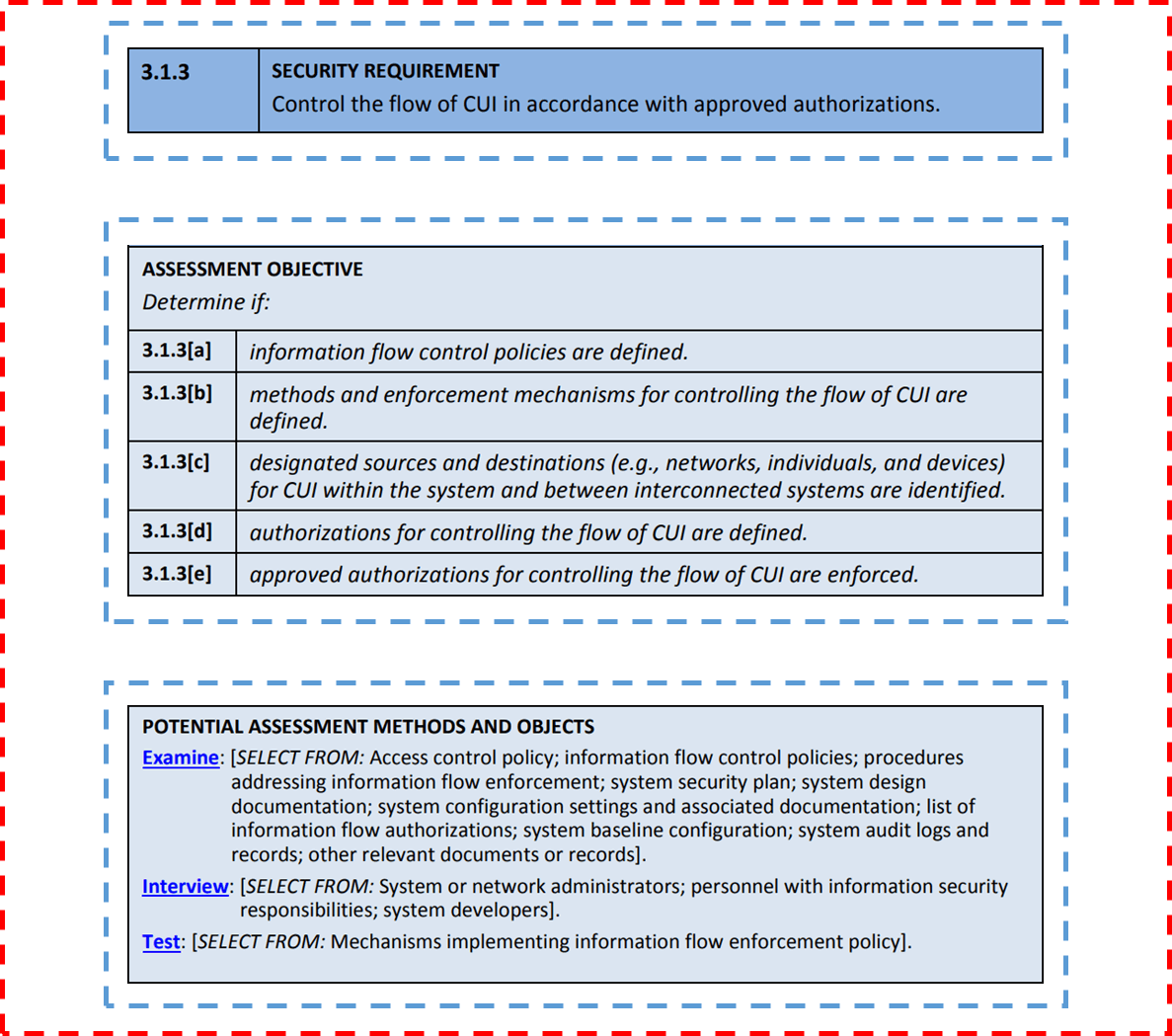
![PDF] Ontology-Based Information Flow Control of Network-Level Internet Communication | Semantic Scholar PDF] Ontology-Based Information Flow Control of Network-Level Internet Communication | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f5a30ed78c732463596bf2853bf596a79ecf08d3/23-Figure14-1.png)
PDF] Ontology-Based Information Flow Control of Network-Level Internet Communication | Semantic Scholar
![PDF] Ontology-Based Information Flow Control of Network-Level Internet Communication | Semantic Scholar PDF] Ontology-Based Information Flow Control of Network-Level Internet Communication | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f5a30ed78c732463596bf2853bf596a79ecf08d3/25-Figure16-1.png)
PDF] Ontology-Based Information Flow Control of Network-Level Internet Communication | Semantic Scholar

Runtime Verification of Information flow: Policy-Based Runtime Verification of Information Flow Control: Sarrab, Mohamed Khalefa: 9783845432748: Amazon.com: Books

PDF) Information Flow Control for Strong Protection with Flexible Sharing in PaaS | Thomas Pasquier - Academia.edu